thick client application security testing paladion|thick client applications vulnerabilities : OEM In this post, I’d like to share my methodology to test thick clients to find security issues. A thick client is a type of application where the bulk of . 14 de jun. de 2022 · Outro momento em que Rhenata Schmidt deixou suas curvas poderosas à mostra foi em outubro do ano passado. Na ocasião, ela posou de biquíni .
{plog:ftitle_list}
Resultado da 23 de out. de 2017 · Capítulo 1. Não há links disponíveis para seu país (United States) 35 membros. Clara e Josafá .
In this post, I’d like to share my methodology to test thick clients to find security issues. A thick client is a type of application where the bulk of . In this article, we will learn about thick client applications, their vulnerabilities and ways to carry out security assessment of these applications. What are thick client . Thick client pentesting involves both local and server-side processing and often uses proprietary protocols for communication. Simple automated assessment scanning is not .
The frequency of Thick Client Application Testing is determined as per the applicable industry security standards for an organization. It also depends upon the Risk Assessment results. However, as an industry best practice, it is recommended to perform these assessments at least once a year or upon a change in the environment.
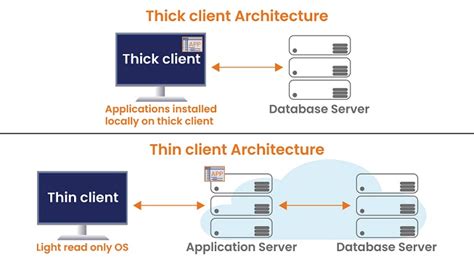
reference in identifying security loopholes in thick client applications. What is Thick Client Application Security? Thick Client Application Overview. Thick client are type of applications which run on user’s host machine/system and communicate with backend server or database server. Few of the examples are listed below: Microsoft Teams .Enhance your cyber security with RBT Security's application penetration testing assessments, covering web, mobile, APIs, Thick Client penetration testing. The Hybrid Infrastructure on which the Thick Client Application usually resides poses more security challenges than web-based thin clients. To put it in simple terms, the Thick Client Application runs on the user’s system, which might not have adequate security measures in place, and attackers can exploit it.
Thick client penetration testing focuses on identifying vulnerabilities within client-server applications where the client-side application (thick client) performs significant processing. Thick client applications can be developed using Java, .Net, C/C++, etc. A thick client may follow two-tier architecture or three-tier architecture. In two-tier architecture, the thick clients directly access the back-end database via the internet. . Thick Client Security Testing - Short Tutorial. by AAT Team Welcome to the Thick Client Penetration Testing Repository! This repository aims to familiarize you with Thick Client Application security concepts, providing a comprehensive guide and practical methodology for thick client Pentesting. Whether you're . Head - Information Security (CISO) at Bajaj Finance Ltd
Attack surface visibility Improve security posture, prioritize manual testing, free up time. CI-driven scanning More proactive security - find and fix vulnerabilities earlier. Application security testing See how our software enables the world to secure the web. DevSecOps Catch critical bugs; ship more secure software, more quickly. Penetration testing Accelerate penetration .
thick client testing

Their extensive use across organizations, often involving critical and sensitive data processing, presents significant security challenges. Thick Client penetration testing is an ethical hacking security assessment carried out to uncover vulnerabilities in the thick client software application, network traffic, and backend interface and . The Thick Client Application Security Testing approach is a highly effective way of testing your client-side software against malware and other threats. The process combines both static and dynamic scanning techniques in order to ensure the safety of the most valuable elements of your application. The results are useful in determining which .
sherwin williams paint test
A thick client, also known as a fat client, is a client application that can provide rich functionality, independent of the server in a network. Thick clients can perform the majority of their functions without a live connection to the server.Thick Client Application Security Many updated applications are handling from the user’s end or from the client-server network nowadays. So, it is your responsibility to protect the thick client applications to avoid the risks and malware. Protection of the applications to transfer the data securely and also protecting database servers is important to run a [.] Welcome to the part 7 of Practical Thick Client Application Penetration Testing using Damn Vulnerable Thick Client App (DVTA). In the previous article, we have discussed how to perform .NET application patching using ildasm and ilasm utilities to modify the functionality of a .NET assembly. In this article, we will discuss DLL Hijacking in .
Testing thick client applications for security vulnerabilities requires expert manual penetration testing skills and a thoughtful, methodical approach. NetSPI’s thick client app penetration testing uses multi-vector cybersecurity testing to identify design and configuration weaknesses.Application Security Audit. Information System Audit and Compliances. Access Control Review. Advisory Services. ISO 27001 Implementation. . Thick Client Penetration Testing (a.k.a. Thick Client Pentest, Thick Client VAPT, Thick .How to identify and exploit common security issues in 2-tier applications. Learn multiple ways to intercept TCP traffic coming from thick client apps. Get real world thick client application penetration testing experience. Learn how to use several .
thick client software
Thick client application security testing involves comprehensively evaluating vulnerabilities, authentication mechanisms, data encryption, security misconfigurations, and network communication . Thick clients can be referenced by many names: Fat Clients, Rich Clients or even Heavy Clients. Such applications follow a client-server architecture and can be developed using various programming .
When it comes to thick client penetration testing, there are several tools that are commonly used by security professionals. One such tool is Burp Suite, which is a powerful platform for performing security testing of web applications.It provides functionalities like intercepting and modifying network traffic, performing code analysis, and executing exploits.Due to their reliance on client-side processing, the security of these applications is heavily dependent on the client. Certbar Security offers specialized testing for thick client applications, integrating both DAST (Dynamic Application Security Testing) and SAST (Static Application Security Testing).
The TASVS Project fills the gap between the OWASP Application Security Verification Standard (ASVS) for web applications and the Mobile Application Security Verification Standard (MASVS). While the MASVS can be applied to thick client testing, it is not an ideal fit. The TASVS Project seeks to create a more suitable standard for these scenarios.
Application Security Testing | Solutions to address security risks at all stages of the application life cycle. DevSecOps | Solutions to help shift security left without slowing down your development teams. Software Supply Chain Security | Solutions to identify and manage software supply chain risks end-to-end.Cybersecurity Solutions. Eviden Cybersecurity Solutions is a comprehensive portfolio of short and long-term engagements that includes cybersecurity strategy, risk & compliance assessment, penetration testing, solution implementation, managed security services, identity services, cloud security, and much more.
Thick client applications can operate without a network connection. To test these applications, you have to understand the entry points for user inputs, application architecture, technologies being used, any propriety protocols, programming languages, and frameworks being used in building it. Read on the blog to know Types of Architecture in Thick . As suggested by Ian, Burp Suite Invisible Proxy mode would be best for capturing request from Proxy unaware Thick client application. Consider an Thick client application making request to www.example.com. Inorder to capture the request through burp the following can be done: Resolving the domain to loopback the local IP address(127.0.0.1).
There are basically 2 types of thick client application. Executables (written in one of either Java, C, C++, .net, etc.) Java applets; Testing of a thick client application. There are three stages in thick client application testing. Dynamic Testing; System Testing; Static Testing; Dynamic testing
thick client security

spray paint test cards
safe home lead paint test kit
19 de abr. de 2014 · 186 - O Beco dos Redemoínhos. Este "percurso" de hoje é para mostrar aos meus queridos amigos e leitores que nem todos os caminhos do meu-nosso Porto são visitáveis. Refiro-me ao Beco dos .
thick client application security testing paladion|thick client applications vulnerabilities